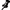BugCheck D1, {0, 2, 1, fffff8800174ec34}
Probably caused by : hardware ( NETIO!KfdClassify+9b7 )
Followup: MachineOwner
---------
2: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If kernel debugger is available get stack backtrace.
Arguments:
Arg1: 0000000000000000, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, value 0 = read operation, 1 = write operation
Arg4: fffff8800174ec34, address which referenced memory
Debugging Details:
------------------
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff8000350d0e0
0000000000000000
CURRENT_IRQL: 2
FAULTING_IP:
NETIO!KfdClassify+9b7
fffff880`0174ec34 db0f fisttp dword ptr [rdi]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xD1
PROCESS_NAME: System
TRAP_FRAME: fffff8800cb1f1a0 -- (.trap 0xfffff8800cb1f1a0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff8800cb1f488 rbx=0000000000000000 rcx=fffff8800cb1f488
rdx=fffffa8006e4ebb0 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8800174ec34 rsp=fffff8800cb1f330 rbp=fffffa8007894d00
r8=0000000000000000 r9=0000000000000000 r10=fffffa800a46f0a0
r11=fffffa8006e4eb90 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
NETIO!KfdClassify+0x9b7:
fffff880`0174ec34 db0f fisttp dword ptr [rdi] ds:0004:00000000`00000000=????????
Resetting default scope
MISALIGNED_IP:
NETIO!KfdClassify+9b7
fffff880`0174ec34 db0f fisttp dword ptr [rdi]
LAST_CONTROL_TRANSFER: from fffff800032d4ca9 to fffff800032d5740
STACK_TEXT:
fffff880`0cb1f058 fffff800`032d4ca9 : 00000000`0000000a 00000000`00000000 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff880`0cb1f060 fffff800`032d3920 : fffffa80`087793d0 00000000`00000000 fffffa80`0b0587c0 fffffa80`08779300 : nt!KiBugCheckDispatch+0x69
fffff880`0cb1f1a0 fffff880`0174ec34 : 00000000`00000000 00000000`00000000 fffffa80`07894d00 fffff880`0cb1f7e0 : nt!KiPageFault+0x260
fffff880`0cb1f330 fffff880`018258de : 00000000`0000000c fffff880`0cb1f7d0 00000000`00000001 fffffa80`0b0587c0 : NETIO!KfdClassify+0x9b7
fffff880`0cb1f6a0 fffff880`0183fd5d : fffffa80`0b0587c0 fffffa80`07894d00 fffffa80`0b988e10 fffffa80`07892071 : tcpip!ProcessInboundTransportLayerClassify+0x21e
fffff880`0cb1f8c0 fffff880`01870fe1 : fffffa80`00000011 fffffa80`0b4a0002 fffffa80`079f2071 00000000`00002871 : tcpip!WfpProcessInTransportStackIndication+0x81d
fffff880`0cb1fc30 fffff880`01840f63 : fffffa80`0b4a9900 fffffa80`07a04380 00000000`00000000 fffffa80`079f9000 : tcpip!InetInspectReceiveDatagram+0x121
fffff880`0cb1fcd0 fffff880`01841315 : fffffa80`0b4a9900 00000000`00000000 fffffa80`07a04380 00000000`00000000 : tcpip!UdpBeginMessageIndication+0x83
fffff880`0cb1fe20 fffff880`0184176d : fffffa80`00000000 fffffa80`0b4a9900 fffffa80`07a04380 fffffa80`0b831c84 : tcpip!UdpDeliverDatagrams+0xd5
fffff880`0cb1ffb0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!UdpReceiveDatagrams+0x1ed
STACK_COMMAND: kb
FOLLOWUP_IP:
NETIO!KfdClassify+9b7
fffff880`0174ec34 db0f fisttp dword ptr [rdi]
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: NETIO!KfdClassify+9b7
FOLLOWUP_NAME: MachineOwner
IMAGE_NAME: hardware
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MODULE_NAME: hardware
FAILURE_BUCKET_ID: X64_IP_MISALIGNED_NETIO.SYS
BUCKET_ID: X64_IP_MISALIGNED_NETIO.SYS
Followup: MachineOwner
Network benchmarking program..